Limited Browser Support: The report-to directive is not implemented in all major browsers yet. For maximum compatibility, it's recommended to use report-uri alongside report-to or rely on report-uriif you need to ensure consistent reporting across all browsers.
report-to
Thereport-to directive is the modern successor to report-uri, designed to provide a more flexible and powerful way to specify endpoints for various security reporting features, including CSP violations.
How it works
When does a violation occur?
A CSP violation occurs when a browser attempts to load a resource that doesn't comply with your Content Security Policy rules. The process works as follows:- The client browser requests your website from the server
- When the browser attempts to load a resource (script, image, etc.)
- The browser checks if the resource is allowed by your CSP rules
- If allowed, the resource loads normally
- If not allowed, the browser blocks the resource and sends a violation report to your specified endpoint

CSP reporting flow diagram
How to collect reports?
When a CSP violation occurs, the browser automatically sends a JSON report to the endpoint specified in thereport-uri directive. These reports contain valuable information about the violation, including the blocked resource, the violated directive, and the page URL where the violation occurred. By analyzing these reports, you can identify and fix your CSP configuration to ensure compliance and security without affecting your users experience.
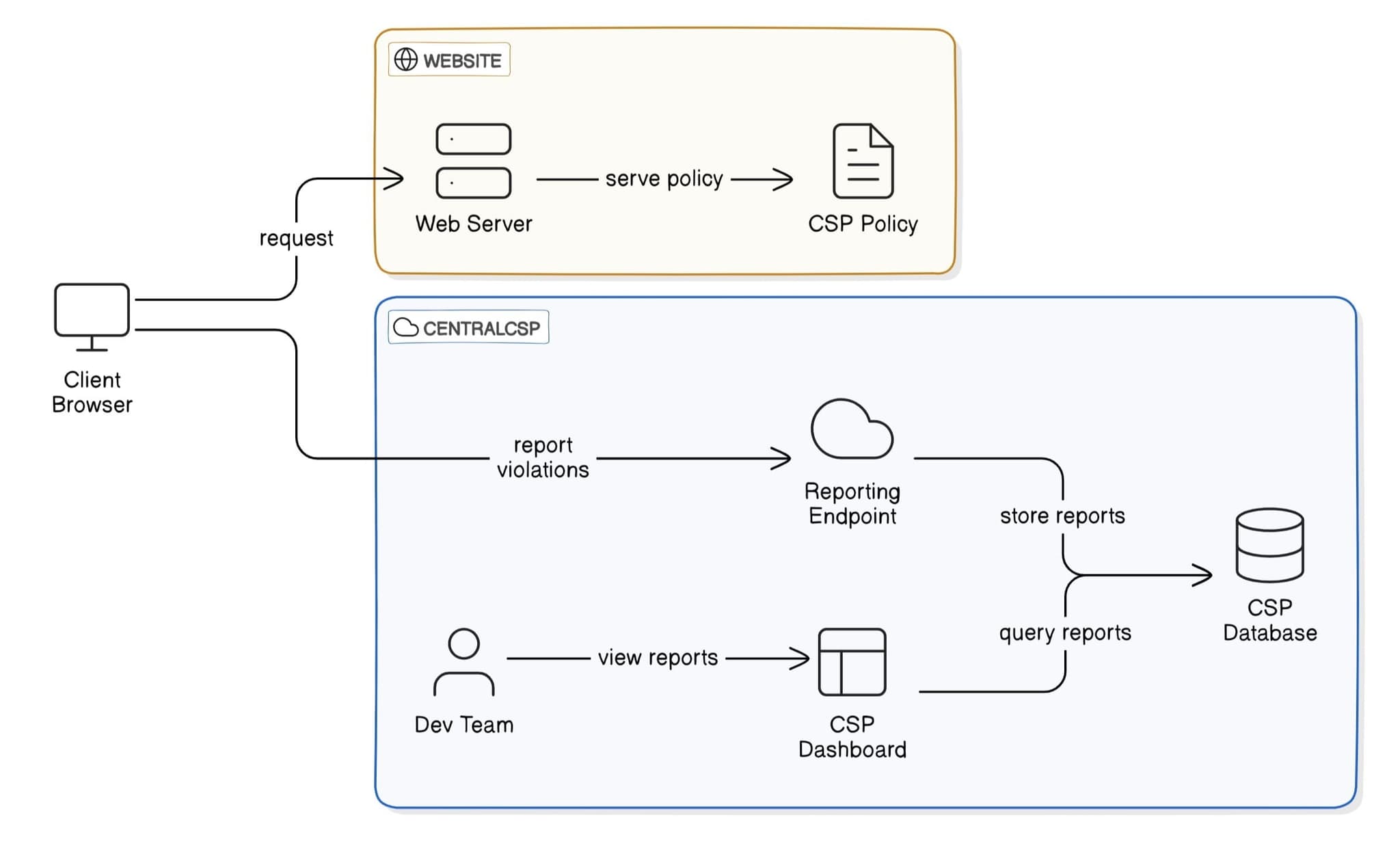
CSP reporting with centralcsp
Current Status
Limited browser support - not all major browsers implement report-to yet
Should be used alongside report-uri for maximum compatibility
How it works
TheReport-To header defines a reporting endpoint group, which can then be referenced by various security features:
Report-To header configuration
Report-To: {
"group": "csp-endpoint",
"max_age": 10886400,
"endpoints": [{
"url": "https://report.centralcsp.com/<yourID>"
}]
}CSP using report-to
Content-Security-Policy: default-src 'self'; report-to csp-endpoint;Browser Support
Current browser support forreport-to:
Chrome/Chromium-based browsers (Chrome, Edge, Opera), Safari
Firefox: Not supported
Recommended Configuration
For maximum compatibility, we recommend using bothreport-to and report-uri:
Recommended configuration using both directives
Report-To: {
"group": "csp-endpoint",
"max_age": 10886400,
"endpoints": [{
"url": "https://report.centralcsp.com/<yourID>"
}]
}
Content-Security-Policy:
default-src 'self';
report-to csp-endpoint;
report-uri https://report.centralcsp.com/<yourID>;Example Report Format
Thereport-to format provides more detailed information compared to report-uri:
Example report-to violation report
{
"age": 0,
"body": {
"documentURL": "https://example.com/page.html",
"referrer": "",
"violatedDirective": "script-src-elem",
"effectiveDirective": "script-src-elem",
"originalPolicy": "script-src 'self'; report-to csp-endpoint",
"disposition": "enforce",
"blockedURL": "https://malicious-site.com/script.js",
"lineNumber": 42,
"columnNumber": 8,
"sourceFile": "https://example.com/page.html",
"statusCode": 0,
"sample": ""
},
"type": "csp-violation",
"url": "https://example.com/page.html",
"user_agent": "Mozilla/5.0 ..."
}Why Use Central CSP for Modern Reporting?
Central CSP is ready for the future of security reporting:- Future-Proof: Support for both
report-toandreport-uri - Enhanced Reports: More detailed violation information
- Unified Dashboard: View all reports in one place
- Smart Analytics: Advanced filtering and analysis
- Automated Monitoring: Real-time alerts and notifications
Get Started with Modern CSP Reporting
Stay ahead with support for both report-to and report-uri directives
Try it nowBest Practices
Always use both report-to and report-uri for maximum coverage
Set appropriate max_age values for your reporting endpoints
Monitor endpoint group configurations regularly
Use HTTPS for all reporting endpoints
Additional Information
- The
Report-Toheader can be used by other security features beyond CSP - Multiple endpoint groups can be defined for different purposes
- Reports are sent asynchronously to avoid impact on page performance
- Endpoint groups can be updated or removed by setting new configurations