Detect all the scripts running on your pages
Get ready for PCI DSS V4 compliance with a complete inventory of scripts running on your pages.
Setup: add report-sha256 (or report-sha384/report-sha512) to your CSP.
Less chasing. More control.
Script Inventory turns “what scripts run on this page?” into a simple, shareable view so audits and reviews don’t derail releases.
Efficiency
A single inventory sourced from real traffic: scripts, origins, and hashes. Faster answers to “what changed?”
Cost / Risk
Spot risky changes earlier with hash changes and known CVE signals. Prioritize fixes before they become findings.
Scalability
Standardize evidence across environments as teams and vendors grow without spreadsheet workflows.
“We finally had a clear list of scripts, hashes, and what changed week to week.”
100%
visibility of scripts loaded on your pages
How it works
Collect integrity reports and turn them into an always-current script inventory.
- 1
Connect your application
Add our reporting endpoint to your CSP. Browsers send integrity reports as pages load.
- 2
View reports and metrics
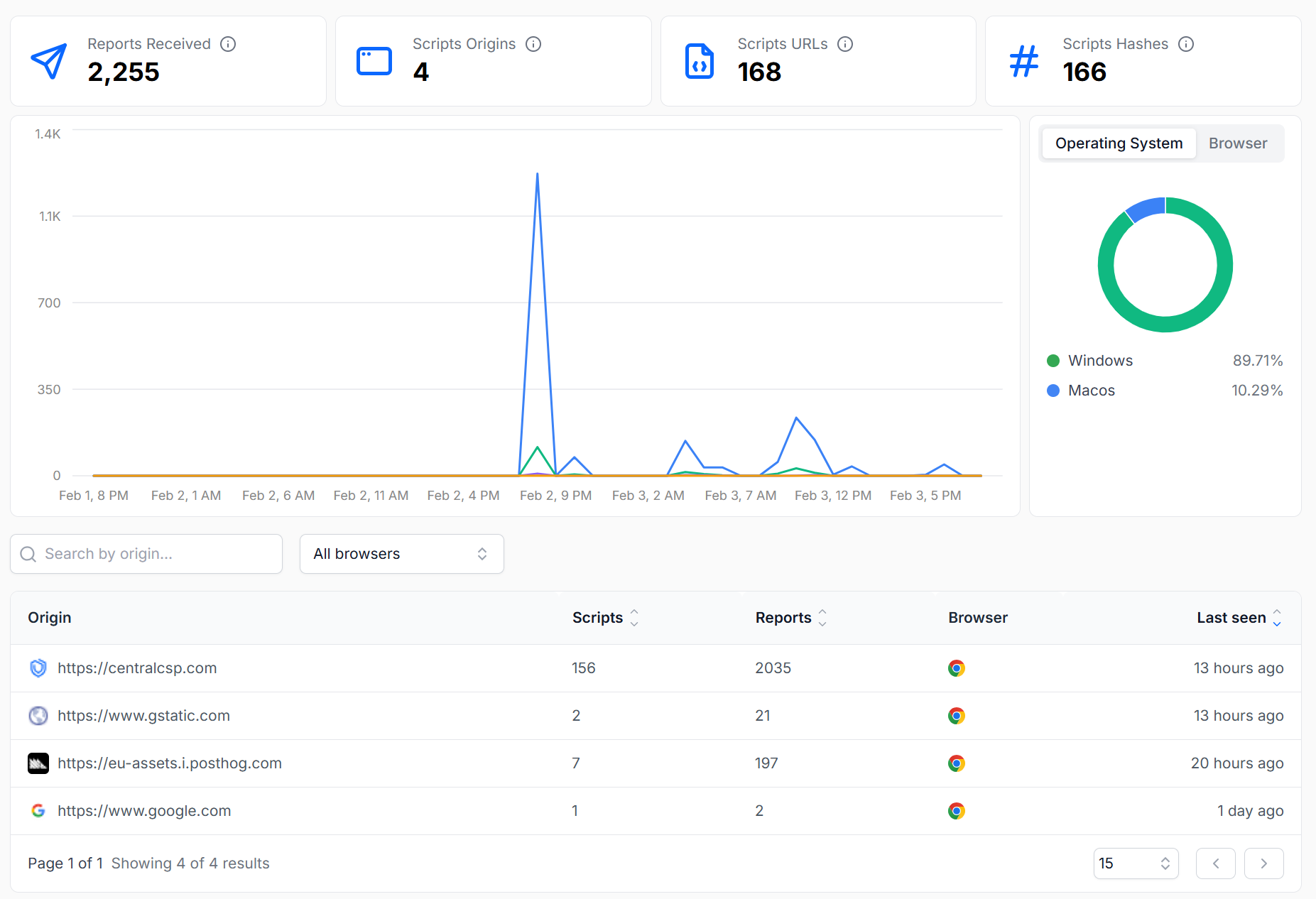
See scripts, origins, URLs, and unique hashes with flexible date ranges.
- 3
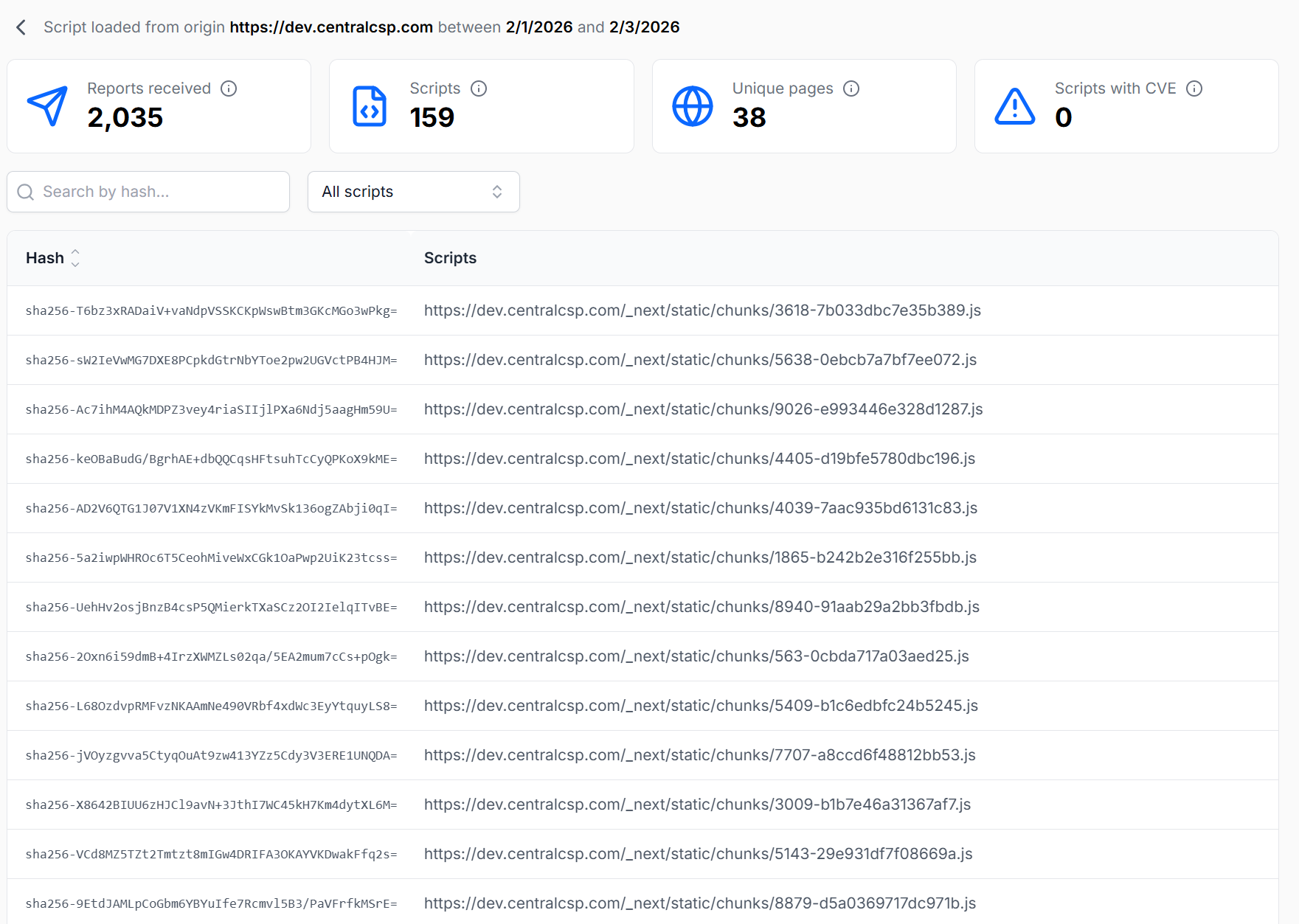
Drill into origins and scripts
Drill into per-origin and per-script details, including known CVE signals.
- 4
Track over time
Track changes over time and catch unexpected additions quickly.
Technical call-out
Minimal example to start collecting integrity reports (adjust directives and endpoint).
Replace <your-endpoint> with your CentralCSP reporting endpoint.
Content-Security-Policy:
default-src 'self';
script-src 'self' 'report-sha256';
report-uri https://report.centralcsp.com/<your-endpoint>;Up and running in 5 minutes.
Add reporting, choose a hash algorithm, and you’re collecting inventory data.
- 1
Connect
Point your CSP reporting to CentralCSP.
- 2
Configure
Pick environments and owners; set alerting if you want it.
- 3
Deploy
Deploy and validate incoming reports in the dashboard.
How Script Inventory compares to the "Old Way"
Side-by-side: manual discovery vs. observed data.
| Metric | Manual / Legacy process | CentralCSP Script Inventory |
|---|---|---|
| Speed | Slow discovery across teams and pages. Re-check after releases. | Updates continuously from real traffic. Changes show up automatically. |
| Accuracy | Easy to miss injected scripts and dynamic loaders. Docs drift. | Built from observed loads so it matches what actually runs. |
| Visibility | Hard to see origin, changes, and risk. | Origin, URL, hash, changes, and known CVE signals per script. |
| Effort | Manual evidence collection before assessments. | Evidence on demand with low ongoing overhead. |
Frequently Asked Questions
Everything you need to know about Script Inventory
Additional Tools
Explore our comprehensive suite of tools designed to help you manage and optimize your Content Security Policy.
Monitor and analyze Content-Security-Policy violations in real-time
Automatically generate a tight policy for your website, based on your website's content.
Monitor all the scripts loaded on your website, their integrity hashes and known CVEs.
Monitor your payment pages for PCI DSS v4.0 compliance.
Get alerted on your favorite channels when a specific event occurs.
Start monitoring your script inventory
Connect your CSP reporting and start capturing script inventory with hashes and CVE signals.